Company
The De Facto Standard for Cloud Governance
Prior to Stacklet, co-founder Kapil Thangavelu created the open source project Cloud Custodian as a way to enforce governance as code similar to the way infrastructure is managed as code with a common language across all major cloud providers. Now a member of the Cloud Native Computing Foundation (CNCF), Cloud Custodian has been adopted by thousands of organizations today including power users such as Intuit, Freddie Mac, FICO, Transamerica, Cox Automotive, Microsoft, Reuters, Amazon, Procter & Gamble, etc. Cloud Custodian’s community is vibrant, active, and rapidly growing.
Simple Policy Language
Simple policy language written in YAML configuration files can be easily understood and used by developers, security, and operations teams alike. Policies can use filters and take appropriate actions on a specific cloud resource or event. These primitives can be used to express thousands of policies easily.
Stateless rules engine
Allows for policy definition and enforcement, with metrics, structured outputs, and detailed reporting for cloud infrastructure. It integrates tightly with serverless runtimes to provide real-time remediation or response with low operational overhead


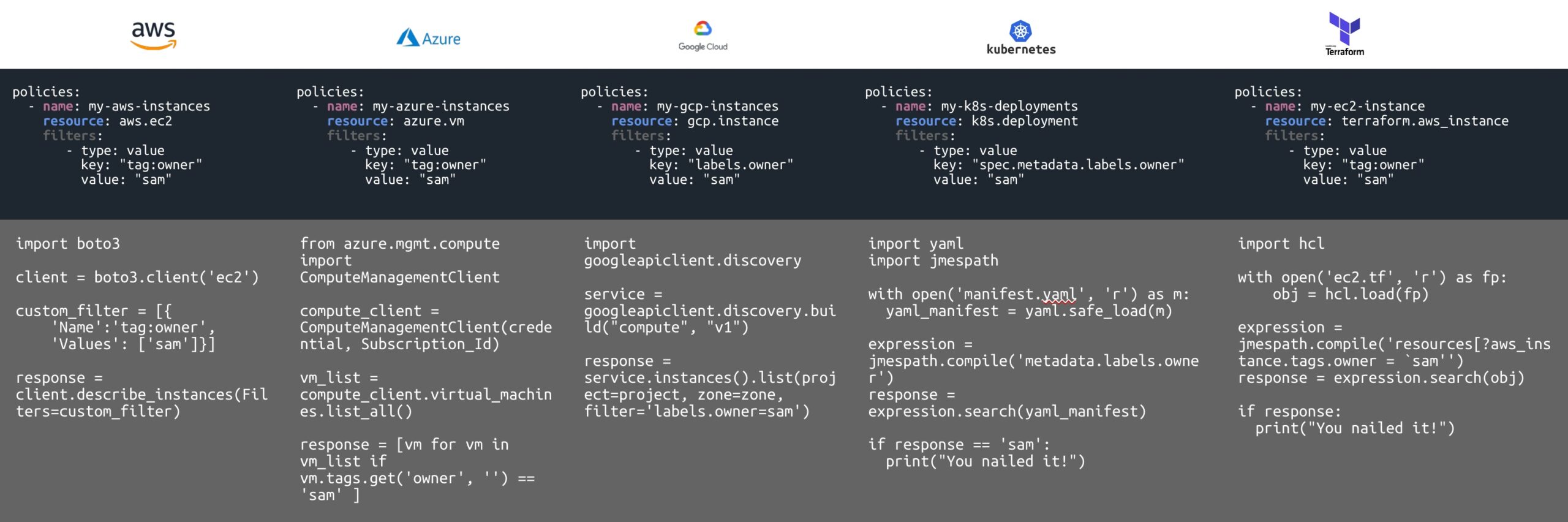
Multi-Cloud Support
Provides integrations with multiple clouds including Amazon Web Services (AWS), Microsoft Azure, Google Cloud (GCP), Oracle Cloud Infrastructure (OCI), and Tencent Cloud. Cloud Custodian supports Over 500+ resources supported across AWS, Azure, GCP, OCI, Tencent Cloud, Kubernetes, and OpenStack.
Open source
Is free to use and is maintained by a thriving community of over 450+ developers and 2000+ chat participants. Cloud Custodian is also part of Cloud the Native Computing Foundation (CNCF), which helps ensure open governance for the project and fosters a diverse community of contributors and end-users.
How does Cloud Custodian Work?
In this video, Kapil Thangavelu, creator and lead maintainer of Cloud Custodian, shares how the project works under the hood (Project Architecture). He covers policy data transmission, resource query process, and the execution modes that govern how a policy will behave when it runs through CLI and what will trigger the policy to execute in the future.
Comparison
Comparing Cloud Custodian and Stacklet Platform

Featured Videos
Learn more about Cloud Custodian.

Governance as code day with cloud custodian 2024 – Hosted by Stacklet
FAQ
Frequently Asked Questions
Here are a few useful links for you to get started
- Getting started Docs: Here is an excellent place for you to learn how to deploy and explore the tool.
- Mailing List: Join the project mailing list for essential project announcements, ask questions and get meeting invites
- Contributing to Cloud Custodian: If you’re interested in contributing to the project, this guide will help.
- Slack Channel: Meet your peers and ask questions by joining this chat channel
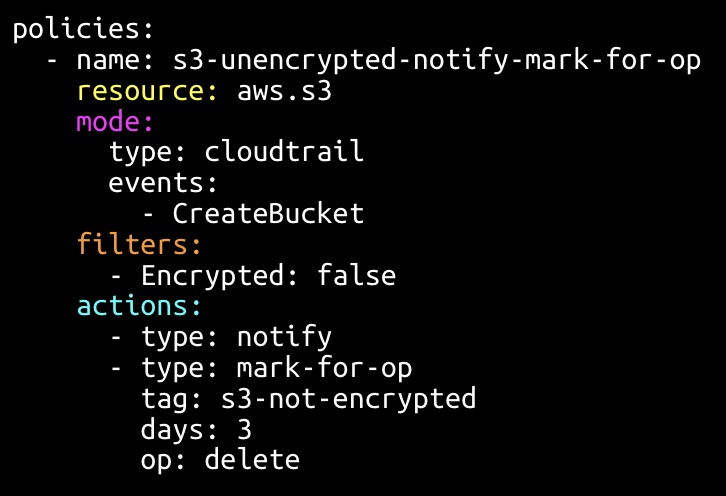
Cloud Custodian can help you enforce a fleet of policies that control cloud costs, avoid potential breaches, and meet regulatory requirements across an ever-increasing number of cloud services and providers. You can review these documents for sample cloud custodian policies.
Cloud Custodian has numerous execution modes, most of which are cloud provider specific. Pull mode policies work across all cloud providers and are the default execution mode if no mode is specified in the policy being executed. Many of the following execution modes work by automatically provisioning serverless functions with the appropriate triggers when the policy is executed. For AWS you can execute policies in the following modes: pull, asg-instance-state, cloudtrail, config-poll-rule, config-rule, ec2-instance-state, guard-duty, hub-finding, periodic, and phd. For Azure you can execute policies in the following modes: pull, azure-event-grid, azure-periodic, container-event, and container-periodic. For GCP you can execute policies in the following modes: pull, gcp-audit, gcp-periodic, and gcp-scc. To see more details on the supported execution modes, see the Cloud Custodian Execution Modes docs – AWS, Azure, GCP.
Cloud Custodian synthesizes the complexity of policy authorship into simple YAML. Each policy is for a specific resource type and consists of a vocabulary of actions and filters that can run in different modes. At the most basic level, each policy must have a name and resource specified. Here is an example tag compliance policy for AWS. View policy
Cloud Custodian has hundreds of built-in actions across its supported resources. At a high level, these actions include things like applying tags to resources, modifying resource attributes, deleting resources, sending notifications, triggering lambda functions, sending webhooks, and a lot more. Many actions are specific to the resource the policy is running against. To see the full list of supported resource actions, see the Cloud Custodian Reference docs – AWS, Azure, GCP.